
There are a few different reasons why Gmail messages will display the “This message seems dangerous” banner, both in your inbox and in emails you send to others. If this is happening to you, there are things you can do to troubleshoot the problem.
However, if you want to know a bit more about why gmail flags some emails (and not others), read on.
why do I see “this message seems dangerous”?
The short answer is that it is impossible to know exactly why gmail marks some emails with this banner. However, here are some potential reasons:
- too many recipients (you will often see this banner appear in email chains).
- bad grammar/punctuation.
- too many attachments.
- too many images.
- too many hyperlinks.
- the sender is already in a database of suspicious email addresses.
- The sender does not have email authentication configured.
- The email does not have an unsubscribe button (or link) and is from a commercial domain.
gmail has not disclosed its exact spam/malicious email detection logic; This is almost certainly so hackers can’t use the information to bypass Google’s filters. however, we do know a few things about gmail’s email filtering technology.

When you send or receive an email, that email travels through Google’s proprietary spam filters before reaching an inbox. there is no way to turn these filters off, which is a good thing. if google deems an email passing through them to be suspicious, the email will be marked with the banner “this message seems dangerous” or sent to the folder from gmail spam.
These filters are really important because email is a common vector for cyber attacks of all kinds, including:
- spear-phishing : malware, exploit, or phishing attacks sent to a targeted recipient.
- malspam : malware, including ransomware , Trojans, and spyware, delivered by email.
- link phishing : Emails disguised as being from a trusted organization that contain links to malicious websites. these websites will steal your information or force you to download dangerous files.
- exploit attacks : emails that contain code that can find a security flaw in your computer, such as -date os. malicious code will use this exploit to open a backdoor into your system and spread malicious files or steal information.
- man-in-the-middle attacks : attacks where hackers intercept emails between trusted organizations or individuals. attackers can use intercepted email to steal information or spy on those involved in the email chain.
You can learn more about common types of email-based attacks later in this article.
if you’re trying to protect yourself from email attacks, you should download an antivirus program instead of relying only on google’s finicky email filters. eg norton 360 has real-time malware scanning, which can prevent malspam attacks, and its secure web browser extension blocks phishing links and malicious sites that can perform exploit attacks. In addition, Norton’s firewall can prevent hackers from accessing your network to launch spear phishing attacks.
“this message seems dangerous” appears in the emails I receive
step 1. check the sender of the email
First, you need to determine whether or not the email is from a trusted source. however, it is important to double check before deciding that it recognizes an email address.
Hackers sometimes disguise your email to make it look like it’s from a trusted company or person. You should check the email address for spelling errors. One strategy hackers use is to replace a character in the address with one that looks similar, such as using the number “0” instead of an uppercase “o” or a lowercase “l (l)” instead of an “i.” ” capital letter. (i).”
Other irregularities to be aware of in email addresses include:
- false sender name.
- domains from countries you are not affiliated with.
- emails from companies you have not subscribed to.
- emails from domains you haven’t heard of.
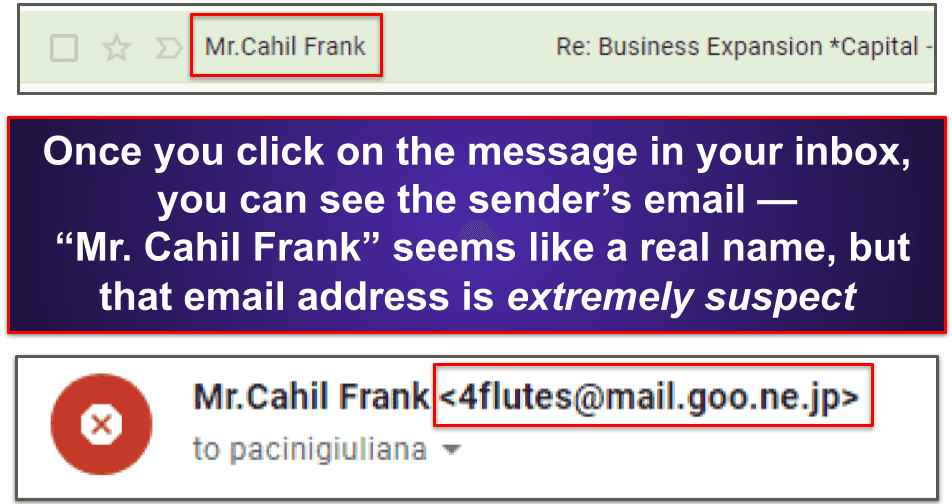
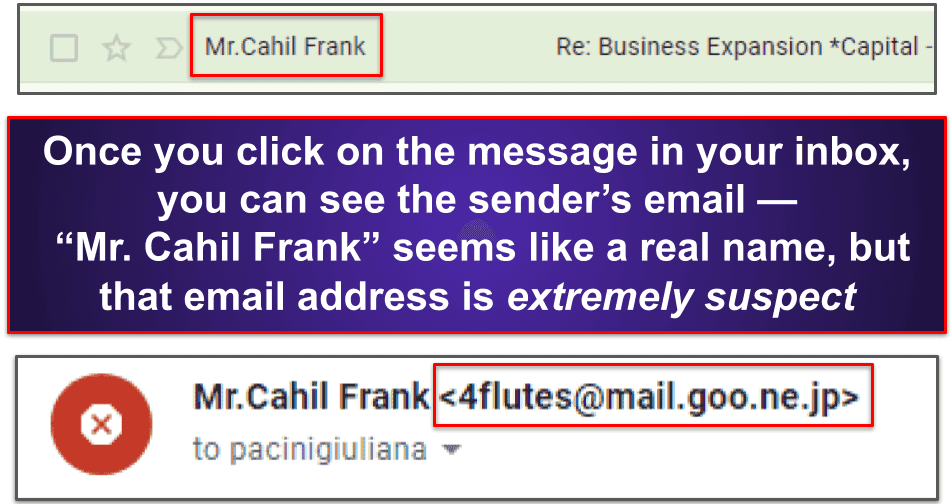
Spoofed sender names are an incredibly common tactic and don’t require much hacking experience. Hackers can spoof an email so that at first glance it looks like you’ve received a message from, say, Amazon Fulfillment. however, when you look closer, the sender’s email address is something like ama.z0n.ful@hotmail.com (which is not a legitimate amazon email address!).
In these situations, you must open the email. The sender’s actual email address will always be displayed in non-bold text above the email subject line:
Also, while you have the email open, look for suspicious signs in the email body content, such as misspelled names and other misspellings. In the example above, the sender assured me that he represented a large corporation “composed of and financed by indigenous investors and lenders.” this is not a legitimate business expansion opportunity (unfortunately).
If you’ve completed the steps above and the email appears to be from someone you’ve corresponded with before, there is one final check you can complete with absolute certainty:
- select compose in the upper left corner of your gmail window.
- Copy the suspicious email address in the a slash.
If the address matches a trusted sender you’ve previously contacted, their email will appear in a drop-down list. If nothing appears, or if the emails in the drop-down list do not match, you most likely received a scam email disguised as being from a trusted sender.
It’s important to know that legitimate senders can still send you malware if your email has been hacked. if you’ve completed all of these checks, but are unsure about an attachment or link sent to you by a trusted correspondent, it’s best to contact them outside of gmail and ask them directly if the email came from them .
once you have completed all the above checks, if you are satisfied with the email, click seems safe and “this message seems dangerous” the banner will disappear. eventually the gmail ai will know that you trust this sender and will stop displaying the banner.
Anyway, if you don’t trust email, don’t click any links in the email, don’t download any attachments, and don’t reply. instead, continue to step 2.
step 2. click report dangerousor report phishing
There are two ways to report email as dangerous. The first is to click report dangerous on the “this message looks like banner dangerous”. however, this option is not always displayed. the alternative way is to press the three vertical gray dots in the upper right corner of your inbox. then, in the drop-down list that appears, click report phishing.
No matter how you report the dangerous email, gmail will display a box asking you to confirm your choice.
When you click the report phishing button, the suspicious email will automatically be moved to your spam folder and alert the google abuse team, helping to prevent future spam. phishing attacks. you can then delete the email or leave it in your spam folder, and it will be deleted automatically in 30 days.
If you downloaded an attachment from the suspicious email, continue to step 3.
step 3. scan your device
download an antimalware suite. You can check out our list of the best antivirus here (norton 360 is my favorite, and avira has a great free option). Once you’ve downloaded a safe antivirus program, run a full disk scan on your computer.
Even if you know where the attached file was downloaded, it’s best to perform a full disk scan. Some malware may replicate itself to hidden locations or infect your system registry as soon as you download it.
A full disk scan will detect, quarantine and remove every copy of the malicious attachment you downloaded. It will also ensure that your device is not infected with any other malware, including spyware and rootkits. , or worms, which can often go unnoticed.
The full scan may take 1-4 hours as your antivirus needs to scan all files and processes on your computer. When your antivirus has alerted you that the scan is complete, every instance of malware on your system will be identified and quarantined.
download norton now
“this message seems dangerous” appears in the emails I send
step 1. clean your emails
Your recipients may see the banner “this message seems dangerous” in an email you’ve sent for a variety of reasons. for example:
- too many recipients (this ad usually appears in email chains).
- bad grammar/punctuation.
- too many attachments.
- too many images.
- too many hyperlinks.
- your email address is in a database of suspicious emails.
- You have not configured email authentication.
- The device you sent the email from is infected with malware .
- The email does not have an unsubscribe button (or link) and is being sent from a business domain.
Google automatically flags emails that meet these criteria as a way to protect users from phishing links. If this is the case, you can try removing images, links and attachments and make sure there are no simple errors in your email.
If you are sending emails with a design element, there may be some code in your email template that is causing your messages to be marked as dangerous. play with the content of your template, remove elements and send test emails to see when the warning appears and when it doesn’t. you can find the source of the problem this way.
If you’re sending business emails to a mailing list, it’s also important to check their bounce and complaint rates. you should keep these values as low as possible by immediately removing any addresses for which you have received a bounce or complaint from your database.
You can also try to send the email to fewer people or use gmail’s blind carbon copy (bcc) feature. using bcc will hide recipients’ email addresses from each other and decrease the chances of gmail flagging your email since you won’t be spreading personally identifiable information (PII).
step 2. configure email authentication
spf, dkim, and dmarc are email authentication methods designed to prove to internet service providers and mail services that you are authorized to send email from a particular domain. verifying your account with spf, dkim and dmarc is very important as google recommends using all three authentication methods.
here is a brief summary of what each record does:
- spf (sender policy framework) – Specifies the number of domain ips allowed to send email from your domain.
- dkim ( mail identified by domain keys) : ensures that no one in the middle interferes with emails going from one server to another, and that the email can be identified at the receiving end.
- dmarc (domain-based message authentication) : An additional layer of validation that matches the validity of spf and dkim records. you can receive dmarc reports if email validation fails.
To check which email authentication methods you have already configured, and to add more methods as needed, you will need to access your DNS settings. the exact processes will vary depending on the email service you are using, so follow the instructions provided. If you use Gmail, here are the details you need to manage email authentication in Google Workspace.
once you’ve followed all the steps above and your email content is clean, send the email to yourself, and only yourself, before sending it to the desired location, to verify that the banner is already not appear.
If the banner continues to appear to your recipients when you send an email, your device may have been infected with malware. in that case, go to step 3.
step 3. scan your device
once you’ve downloaded a safe antivirus program, run a full disk scan on your computer.
Viruses and other malware can take control of your device and send themselves as attachments to other users on your network. These users often download and run the attachments they get from your device because they trust your email address.
running a malware scanner will allow you to prevent the virus from hacking your emails and can also tell you what kind of malware is on your device. In this way, you can help keep your email recipients safe by warning them about the specific risks they face.
If you detect malware or someone on your network notifies you that you’ve been sending suspicious links or attachments, be sure to check your sent folder. you can then notify others in your network to ignore your previous hacked emails.
The full scan may take 1-4 hours as your antivirus needs to scan all files and processes on your computer. When your antivirus has alerted you that the scan is complete, every instance of malware on your system will be identified and quarantined.
download norton now
common types of email-based attacks
Emails are one of the most common tools used for cyber attacks, and while many email clients like gmail have built-in spam filters, they cannot protect you from all email-based threats. .
via email, you can be a victim of the following attacks:
spam
malspam is the general term given to malicious files distributed by email in the form of attachments. this is one of the most common ways malware spreads. according to a cso study, 94% of malware is delivered via email.
via malspam, your computer can be infected with:
- Trojan horses: legitimate-looking files that steal or modify data on your computer.
- computer worms: viruses that spread they replicate themselves on your computer, drain your cpu and modify or delete files.
- ransomware : locks and encrypts files on your computer. often the hacker will ask for money before unlocking your files.
- rootkits – allows hackers to take control of your computer remotely.
- cryptojackers : they hide from the user and silently steal their cryptocurrencies.
- and more…
link phishing
Link phishing emails trick users into thinking they are receiving official communications from a trusted company, but actually contain links to malicious phishing sites. These sites are designed to steal your personally identifiable information (PII), or even your financial information.
These emails are often disguised as fake versions of popular websites like netflix and threaten to deactivate your account unless you enter your payment details. This type of attack is so common that Netflix even has a page set up to deter people from falling for it.
spear-phishing
Spear phishing attacks are email attacks that target specific recipients. Hackers investigate a victim’s networks, software, company procedures, and more to make sure that its payload hits the target. that means it will be easy to fall for malicious email containing specific malware and exploits to target your systems.
Spear-phishing is typically targeted at high-value targets such as corporations, banks, and executives. In fact, even Google and Facebook have fallen for this email scam. Between 2013 and 2015, a shell corporation created by hackers sent spear phishing emails to financial executives at both companies, tricking them into transferring around $100 million for counterfeit services.
man-in-the-middle (mitm) attacks
A mitm attack occurs when a hacker inserts himself into the communication between two trusted sources, without being detected by either of those sources. These sophisticated attacks can be used to eavesdrop on conversations or even intercept and alter communications between two users.
for example, in 2019, an israel-based startup lost $1,000,000 of seed funding when an mitm hacker altered emails between the startup and a venture capital firm in china. the vc company and the startup thought they were communicating with each other, and the chinese company transferred the funds to what they thought was the startup. however, the attacker had largely rewritten the entire conversation and the bank transfer was actually sent to his account.
anti-malware software can protect you from email-based attacks
The best antiviruses on the market in 2022 provide real-time threat protection that can detect malware files before they are downloaded. they can also block and prevent exploit-based network intrusion with powerful firewalls and host intrusion prevention systems (hips). While no security solution is 100% secure, you can significantly increase your chances of staying safe online by downloading an anti-malware solution.
how to fix “this message seems dangerous”?
If you see “this message looks dangerous” in the emails you send, you may be a victim of malware. Alternatively, your email may have an unnecessary clutter that is being flagged by gmail. Either way, you should follow our steps to remove “this message seems dangerous” and download a good antivirus like norton 360 to protect yourself from future threats.
However, if the banner appears in the emails you receive, you should look at the sender and see if you recognize the address. Keep in mind that hackers often disguise your email to impersonate a trusted company or person. there are several common sense techniques that can help you determine the authenticity of a sender. you can read about them in the steps listed above.
If I see “this message looks dangerous”, does that mean the email contains a malicious link?
not necessarily: gmail flags messages for a variety of reasons. it may simply be that the email has many attachments, contains many images and links, or has been sent to many recipients at You’ll often see “this message seems dangerous” in email chains sent to friends and family, for example.
When in doubt, don’t take any chances. If you don’t recognize the sender of the email, don’t click any links. instead, report the email as phishing. this will alert the google abuse team and move the email to your spam folder.
what do I do if I download an email attachment that shows “this message seems dangerous”?
If you download an email from an attachment that shows “this message seems dangerous”, you may be a victim of malware, especially if you don’t recognize the sender .
In this situation, you should scan your computer for viruses using a good antivirus package such as norton 360. If the attachment you downloaded is malicious, Norton 360 Malware Scanner will scan your drive and find any instances of it. it will then quarantine the file and any other malware it finds.
norton 360 also has real-time protection and a firewall, which will prevent you from downloading attachments containing malicious files in the future. norton offers a generous 60-day money-back guarantee, so you can try it risk-free.
