The goal of email phishing is to trick users into thinking the email is from someone they know or can trust; in most cases, a colleague, a supplier or a brand. Exploiting that trust, the attacker asks the recipient to divulge information or take some other action.
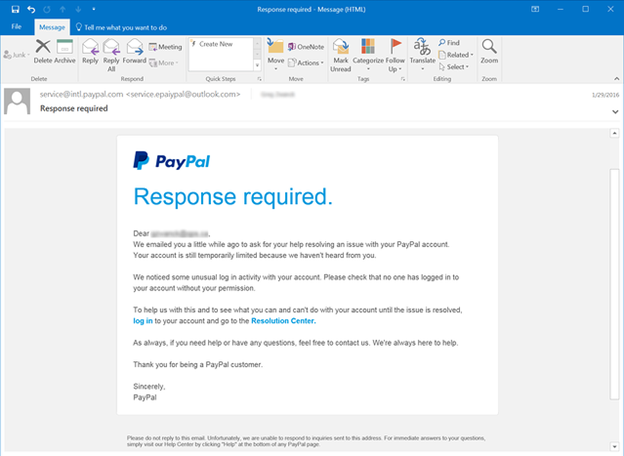
As an example of email phishing, an attacker could create an email that appears to come from paypal. the message tells the user that their account will be suspended if they don’t click a link, authenticate to the site, and change their account password. If the user is successfully tricked into typing in his credentials, the attacker now has credentials to authenticate to the target user’s paypal account, which could potentially steal money from the user.
The most complex attacks target financial employees and use social engineering and online reconnaissance to trick a targeted user into sending millions to an attacker’s bank account.
To the user, a spoofed email message appears legitimate, and many attackers will take elements from the official website to make the message more credible. here is an example of email phishing with a paypal phishing attack:
With a typical email client (such as Microsoft Outlook), the sender’s address is automatically entered when a user sends a new email message. but an attacker can programmatically send messages using basic scripts in any language that sets the sender address to an email address of their choosing. email api endpoints allow a sender to specify the sender’s address regardless of whether the address exists. and outgoing email servers cannot determine if the sender’s address is legitimate.
Outgoing email is retrieved and routed using the Simple Mail Transfer Protocol (SMTP). when a user clicks “send” in an email client, the message is first sent to the outgoing smtp server configured in the client software. the smtp server identifies the recipient’s domain and routes it to the domain’s email server. the recipient’s email server routes the message to the correct user’s inbox.
For every “hop” an email message takes as it travels across the Internet from one server to another, the IP address of each server is logged and included in the email headers. these headers disclose the true path and sender, but many users do not check the headers before interacting with an email sender.
The three main components of an email are:
– the sender’s address
– the address of the recipient
– the body of the email
another component often used in phishing is the response field. this field is also configurable from the sender and can be used in a phishing attack. the reply-to address tells the client’s email software where to send a reply, which may be different from the sender’s address. again, email servers and smtp protocol do not validate if this email is legitimate or spoofed. it’s up to the user to realize that the reply is going to the wrong recipient.
here is an example of a spoofed email:
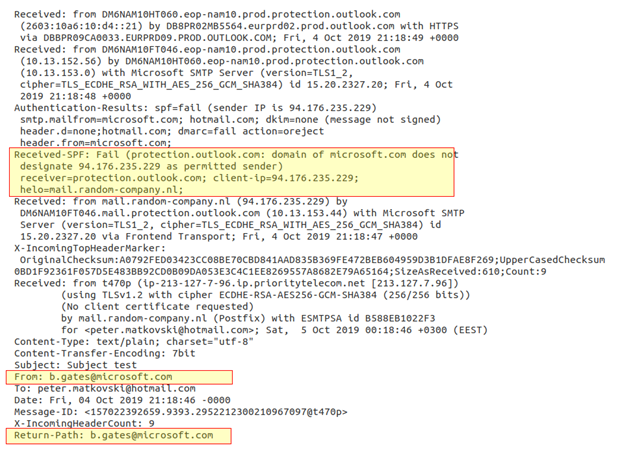
Note that the email address in the sender field is supposed to be bill gates (b.gates@microsoft.com). There are two sections in these email headers to review. the “received” section shows that the email was originally handled by the email.random-company.nl email server, which is the first clue that this is an email phishing case. but the best field to check is the received spf section: note that the section has a status of “failed”.
sender policy framework (spf) is a security protocol established as a standard in 2014. It works together with dmarc (domain-based message authentication, reporting, and conformance) to stop malware and phishing attacks.
spf can detect spoofed emails and has become common in most email services to combat phishing. but it is the domain owner’s responsibility to use spf. To use spf, a domain owner must configure a dns txt entry that specifies all the ip addresses authorized to send email on behalf of the domain. With this DNS entry configured, the recipient’s email servers look up the IP address when they receive a message to make sure it matches the email domain’s authorized IP addresses. if there is a match, the received spf field shows an approval status. if there is no match, the field displays an error status. Recipients should check this status when they receive an email with links, attachments, or written instructions.
