what is “gmail virus”?
There are many spam email campaigns used by scammers who try to trick people into providing sensitive details and personal information (logins, passwords for multiple accounts, credit card details, etc.).
Emails are usually presented as legitimate and official: cyber criminals (fraudsters) pose as representatives of well-known companies or services. in this case, google gmail.

“gmail virus” overview
an example is “gmail uk lotto 6/49“. This scam attempts to trick recipients into believing that their email addresses have been selected as winners of a large sum of money (£700,000.00). in this case, they are encouraged to claim their prize by contacting “agents” via the email address or phone numbers provided.
Once contacted, the scammers behind these spam campaigns will attempt to obtain personal information such as bank account details. in other cases, people may be encouraged to open fake (official-looking) websites and provide personal details. for example, log into an account by providing your real usernames/id and passwords.
These emails may contain attachments or links to websites that, once opened, download and install various malware. these programs are also used to generate income by stealing personal data. scammers often send identical emails to many people in the hope that someone will fall for them.
They design their spam campaigns to make it look like the recipients of the email message are just individuals. in this, they try to give the impression that the email is personal. Recipients are advised not to contact anyone about receiving such email.
For example, scammers advise people to keep winner information confidential until the claim is processed, and so on. they do so to minimize the risk of exposure.
many fake winner notifications, lotteries, surveys and other similar scams mention the gmail service; however, google has nothing to do with any of these scams and none can be trusted. an example of another scam distributed using google’s name is “google winner”.
To remove possible malware infections, scan your computer with reputable antivirus software. Our security researchers recommend using Combo Cleaner.▼ Download Combo Cleaner To use the full-featured product, you must purchase a license for Combo Cleaner. 7 days free trial available. combo cleaner is owned and operated by rcs lt, the parent company of pcrisk.com read more.
spam campaigns in general
These scams are used to generate revenue and thus cause financial loss to regular users. This often happens when people take these emails seriously and provide information to scammers.
In some cases, emails contain files (attachments) that, once opened, download and install high-risk computer infections, which then steal personal data. some examples of malicious programs of this type are trickbot, emotet, azorult and adwind.
how do spam campaigns infect computers?
If a spam campaign (email) contains an attachment or a link to a website, it can cause problems only if it is opened. To spread computer infections via emails, cybercriminals use Microsoft Office from pdf documents, files like zip, rar, javascript files, executables (.exe files), etc.
These attachments are usually presented as legitimate files; however, once opened, they download and install other computer infections. These programs are used to steal personal data such as passwords, logins, browsing history data, bank account details, etc. misuse of this information leads to financial loss.
how to prevent installation of malware?
Emails received from unknown or suspicious addresses should not be trusted. They usually present themselves as “official”: scammers use names of well-known companies and claim to be their representatives or people who work there. in fact, these emails are irrelevant (they do not concern their recipients).
If such an email contains a web link or attachment, it should not be opened. download software using official websites and direct links. do not trust third party downloaders, installers, unofficial pages and peer-to-peer networks. also, downloads and installations must be successful.
Check all available settings, such as “custom”, “advanced” and other similar parts, and decline offers to install any unwanted software. use ms office version 2010 or later, as newer versions include “protected view” mode, which prevents infected documents from downloading and installing malware.
Have reliable anti-virus or anti-spyware software installed and keep it enabled at all times. This software generally helps people to keep their computers protected from various threats. If you have already opened malicious attachments, we recommend that you run a scan with a combo antivirus cleaner for windows to automatically remove infiltrated malware.
text presented in an example of a fake gmail lottery notification:
gmail uk lotto 6/49, lottery promotions. telfax: +441633817777 173 greengate, cardale, park, harrogate, hg3 1gy.re: winner notification congratulations!!! your email address won £700,000.00 gbp from: gmail uk lotto 6/49 promotions, held in the uk. to promote international powerball with uk freelotto services and email network services. reference number: gul70q/16two (2) email addresses were selected from one million email addresses and your email address is among the three winning email addresses in the winning pot, which was attached to the number pin: 719, which ultimately won you the sum of £700,000.00 {just seven hundred thousand pounds sterling} our rockers brokers agent will process your cash prize to the paying bank for transfer to you via electronic funds transfer (eft) to your designated bank account or when you receive your ATM card. You are advised that the funds cannot be deducted due to the insurance policy placed thereon, until the aforementioned cash prize reaches the designated bank account of the sole winner/beneficiary for security reasons. visit: www.lottolore.com/lotto649.html with winning number: 9 -12 -15 -20 -25 -45 and bonus number: 16. for security reasons, we recommend all winners to keep winning information confidential from the public until your claim is processed and your prize is awarded. this is part of our security protocol to avoid double claims and unjustified advantages of this program by unofficial or non-participating personnel. To process your cash award release, you must contact our agent, Rockers Brokers, with details below: Rockers Brokers Agent. 3 kemble st, london, wc2b 4ts, united kingdom. agents: mrs. dina emir phone: +44 8447748847 telfax: +44 8447748847 email: dina@rockers.co.uk we recommend that you send your winning and reference number to the broker who will facilitate the payment of the cash prize. Other broker’s agent email: rockersba@yandex.com
Instant automatic malware removal: Manual threat removal might be a lengthy and complicated process that requires advanced computer skills. combo cleaner is a professional automatic malware removal tool and is recommended to get rid of malware. download it by clicking the button below: ▼ download combo cleaner By downloading any software included on this website, you agree to our privacy policy and terms of use. To use the full-featured product, you must purchase a license for Combo Cleaner. 7 days free trial available. combo cleaner is owned and operated by rcs lt, the parent company of pcrisk.com read more.
quick menu:
- what is “gmail virus”?
- step 1. manual removal of possible malware infections.
- step 2. verify that your computer is clean.
how to remove malware manually?
Manual malware removal is a complicated task; it’s usually best to let antivirus or antimalware programs do this automatically.
To remove this malware, we recommend using the antivirus combo cleaner for windows. If you want to remove malware manually, the first step is to identify the name of the malware you are trying to remove. here is an example of a suspicious program running on a user’s computer:
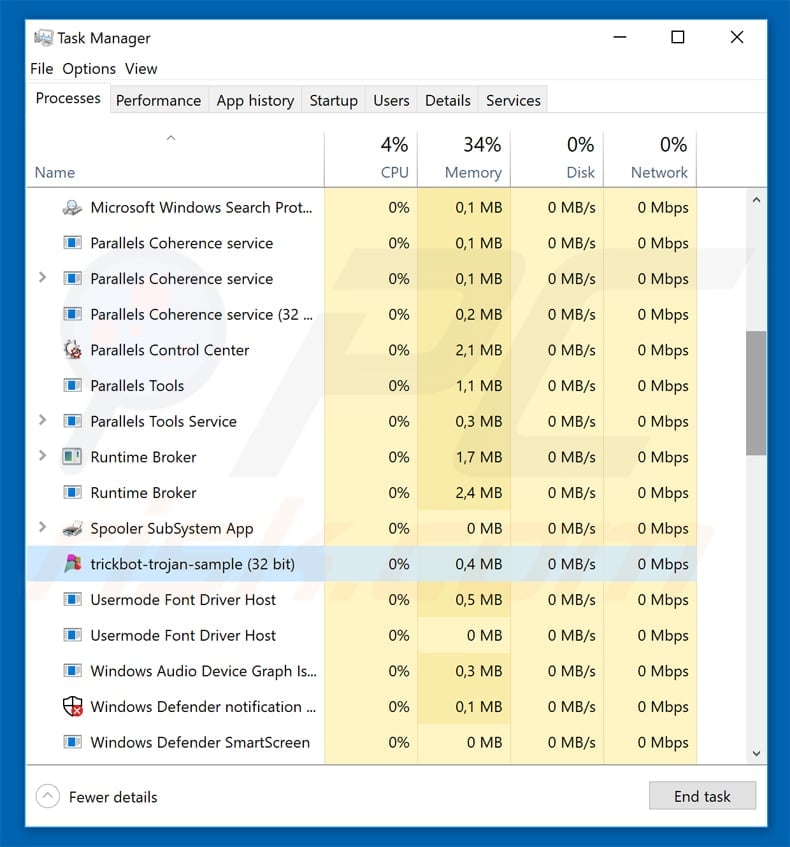
If you have checked the list of programs running on your computer, for example using Task Manager, and have identified a program that seems suspicious, you should continue with these steps:
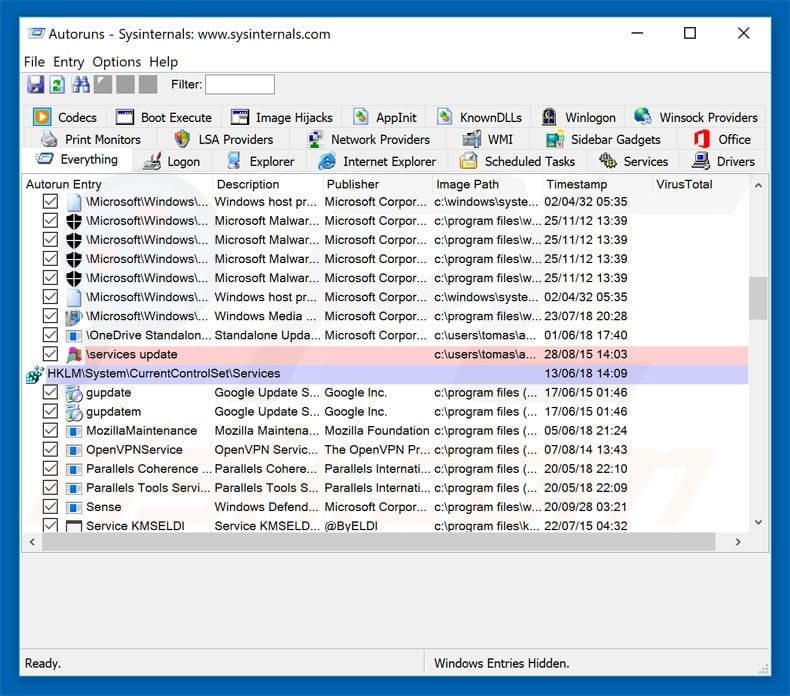
download a program called autoruns. this program shows autostart applications, registry and file system locations:
restart your computer in safe mode:
windows xp and windows 7 users: start your computer in safe mode. click start, click shutdown, click restart, click ok. During your computer’s startup process, press the f8 key on your keyboard several times until you see the windows advanced options menu, and then select safe mode with networking from the list.
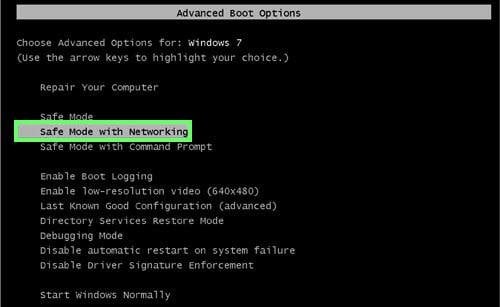
video showing how to start windows 7 in “safe mode with networking”:
windows 8 users: start windows 8 in safe mode with networking: go to the windows 8 start screen, type advanced, in the search results, select settings. click advanced startup options, in the opened window “general pc settings” select advanced startup. click the “restart now” button.
your computer will now reboot to the “advanced boot options menu”. click the “troubleshoot” button and then click the “advanced” button. On the advanced options screen, click on “startup settings”. click the “reboot” button. your pc will reboot to the boot settings screen. press f5 to boot into safe mode with networking.
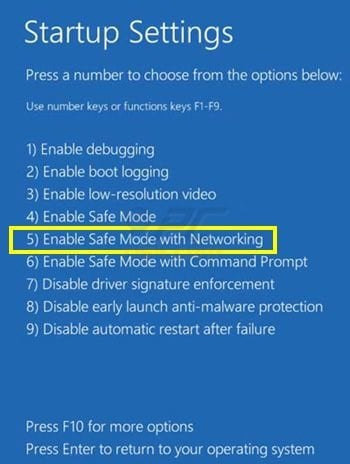
video showing how to start windows 8 in “safe mode with networking”:
windows 10 users: Click the windows logo and select the power icon. in the opened menu, click “restart” while holding down the “shift” button on your keyboard. in the “choose an option” window, click “troubleshoot”, then select “advanced options”. in the advanced options menu, select “startup settings” and click the “restart” button.
in the next window you should click on the “f5” button on your keyboard. this will reboot your operating system in safe mode with networking.
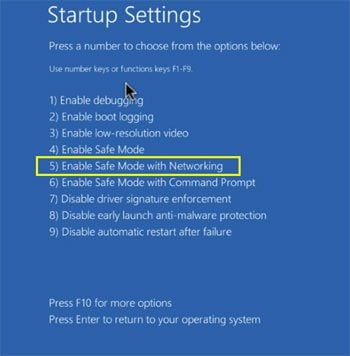
video showing how to start windows 10 in “safe mode with networking”:
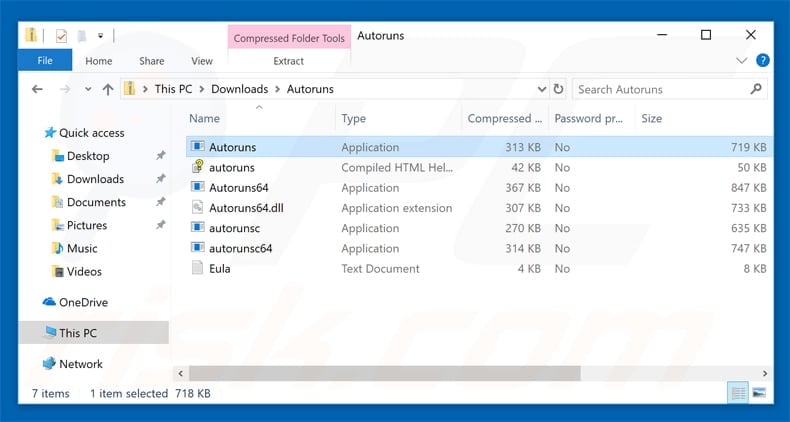
extract the downloaded file and run the autoruns.exe file.
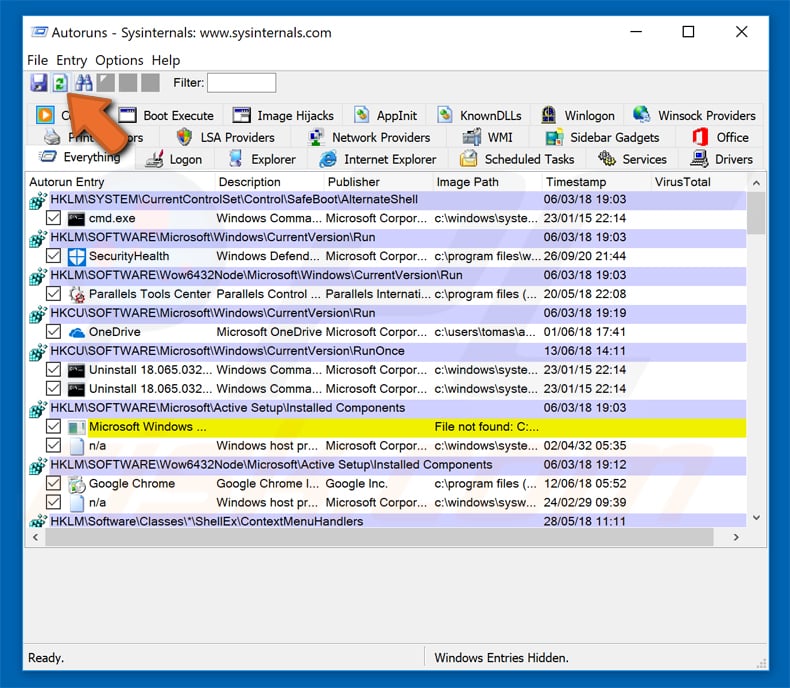
In the autorun application, click “options” at the top and uncheck the “hide empty locations” and “hide window entries” options. after this procedure, click the “refresh” icon.
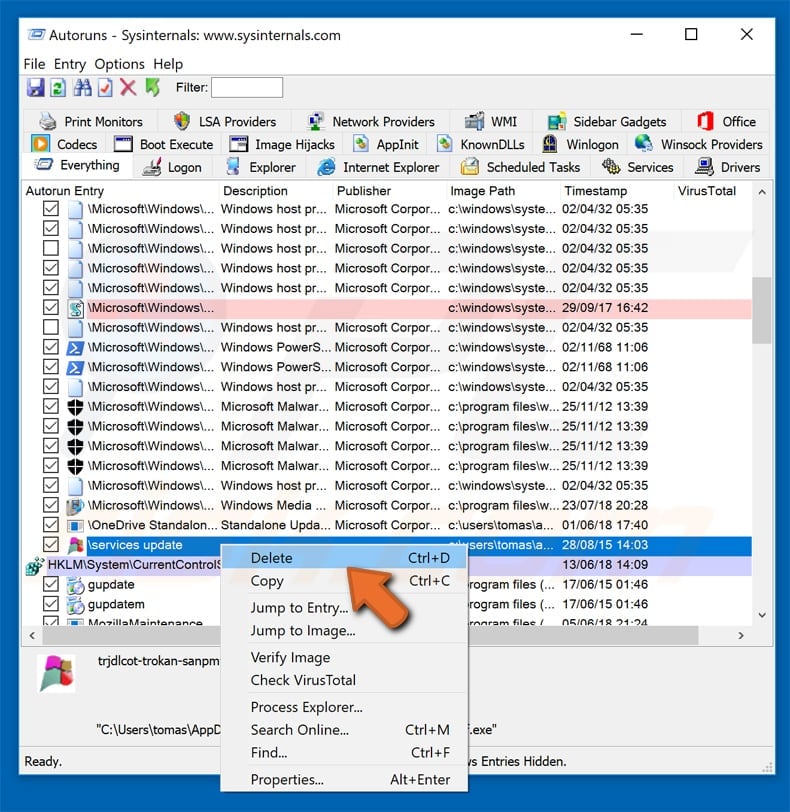
Refer to the list provided by the autorun application and locate the malware file you want to remove.
You should write down your full path and name. Please note that some malicious programs hide process names under legitimate windows process names. At this stage, it is very important to avoid deleting system files. after locating the suspicious program you want to remove, right-click on its name and choose “remove”.
after removing the malware via autorun application (this ensures that the malware will not automatically run at the next system startup), you need to search your computer for the name of the malware. make sure you enable hidden files and folders before continuing. if you find the malware file, be sure to remove it.
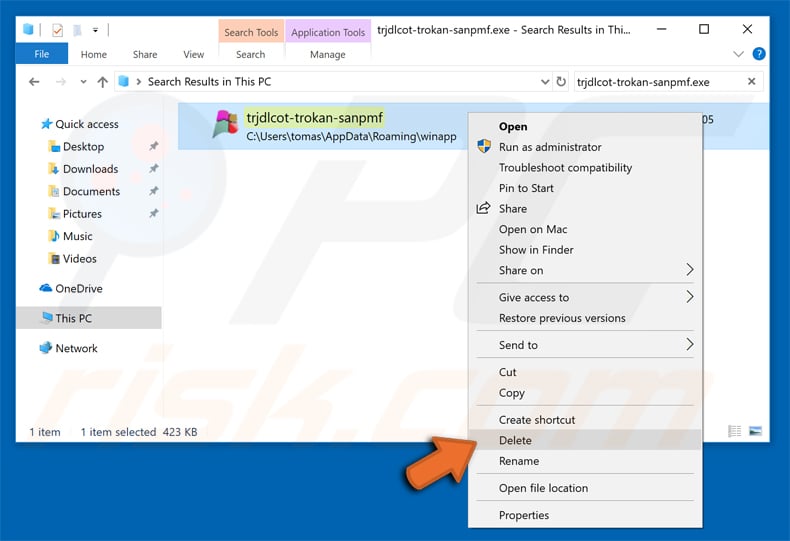
restart your computer in normal mode. Following these steps should remove any malware from your computer. Please note that manual threat removal requires advanced computer skills. if you don’t have these skills, leave malware removal to antivirus and antimalware programs.
These steps may not work with advanced malware infections. As always, it is better to prevent infection than to try to remove malware later. To keep your computer secure, install the latest operating system updates and use antivirus software.
To ensure that your computer is free from malware infections, we recommend that you scan it with antivirus combo cleaner for windows.
frequently asked questions (faq)
why did I receive this email?
Spam emails are not personal. cybercriminals distribute them in massive operations; therefore, thousands of users receive identical cards.
I provided my personal information when I was tricked by this spam email, what should I do?
If you have disclosed login credentials, please change the passwords of all potentially exposed accounts and inform your official support without delay. and if you have disclosed other private information (eg, ID card details, credit card numbers, etc.), immediately contact the appropriate authorities.
I read a spam email but didn’t open the attachment, is my computer infected?
If you have simply opened/read a spam email, no, your system is not infected. Malware download/installation processes are started when attachments or links in this email are opened or clicked.
I downloaded and opened a file attached to a spam email, is my computer infected?
if it was an executable (.exe, .run, etc.), then most likely yes, your system was infected. but it could have avoided triggering an infection chain if it was a document (.doc, .xls, .pdf, etc.), as these formats may require additional user interaction (eg enabling macro commands) to start downloading/installing malware.
will combo cleaner remove malware infections present in email attachments?
yes, combo cleaner is capable of detecting and removing most known malware infections. It should be emphasized that running a full system scan is paramount, as high-level malware tends to hide deep within systems.
